Maximizing QR Code Security: Top 5 Mistakes and How to Fix Them
- Rajesh Soundararajan
- May 17, 2022
- 4 min read
QR Code Document Security: Avoid These 5 Common Mistakes
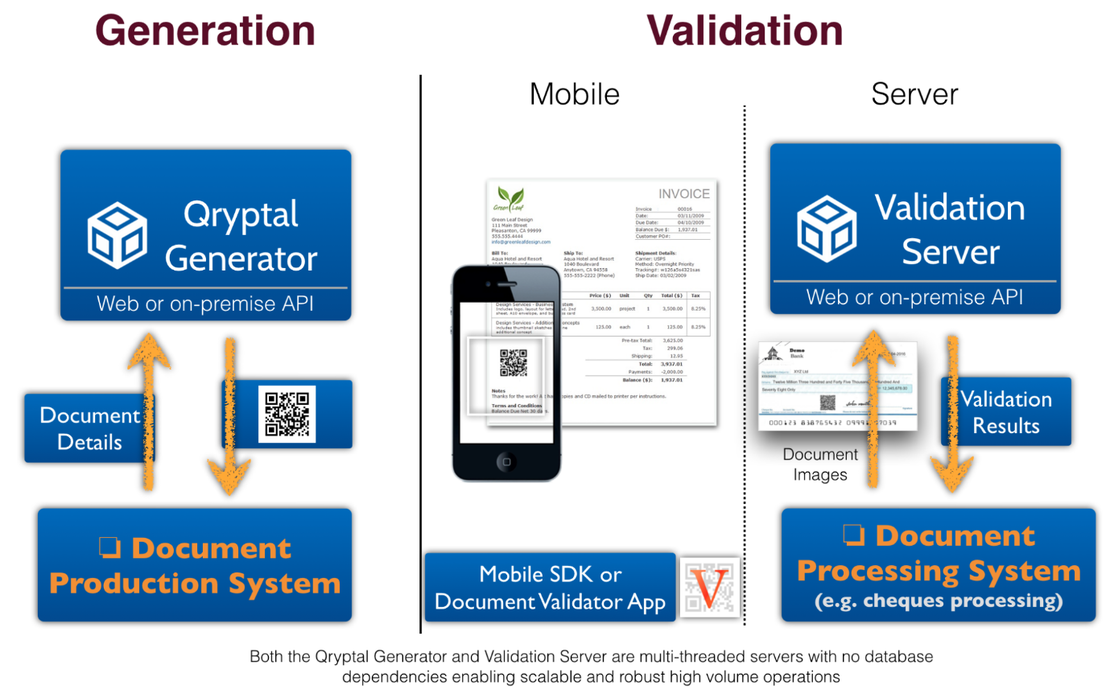
Document security muyst be a top priority, and your QR code strategy should be well-planned and executed. QR codes are used for various purposes, from simple ID cards to payments, warranty cards, insurance policies, and educational documents. Ensuring document security is the core purpose of these codes.
Many organizations overlook the importance of having a well-defined strategy for QR codes, especially for document security. Secure QR codes are essential for any organization, whether government or private. These codes can be found on ID cards, invoices, purchase orders, or insurance policies requiring third-party validation. The issuer must ensure the document’s authenticity, which should be easily verifiable.
This article discusses five common mistakes to avoid when using QR Codes for document security, providing a solid starting point for your strategy.
MISTAKE #1: Having a QR Code Just Because Everyone Has It
Here’s what you can do:
Solution: Consider functionality, security, and ease of use when designing your document security solution. Ensure that the QR code offers security and authentication while being easy to implement and integrate with existing document generation systems.
MISTAKE #2: Treating Your QR Code as a One-Time Static Image
A QR code is not just an image, a URL link, or a barcode. It’s a secure digital access point that can include updated information over time. Forgetting this aspect can lead to suboptimal solution design.

Here’s what you can do:
Solution: Remember that a QR code can provide comprehensive, updated information without giving users access to your IT systems or databases. This feature is essential for situations where information needs to be updated, such as ID cards, health certificates, or insurance policies. We have an article on this - 4 Questions to ask before implementing QR Codes.
MISTAKE #3: Not Looking at It from the Verifier’s Point of View

The most thought-out QR Code solution will always keep the document holder and verifier’s point of view at the forefront and design the document security solution accordingly.
Here’s what you can do:
Solution: Ensure that the QR code is easily scannable and provides necessary information for verification. Make the verification process as seamless as possible for the verifier, including simple instructions and take into account the operating environment for verification - whether digital or physical would work etc.
MISTAKE #4: Not Being Clear on Functionality and Extensions

Here’s what you can do:
Solution: Familiarize yourself with different types of QR codes and their respective functions, such as static, dynamic, and secure QR codes. Understand how they can be customized to meet your organization’s specific needs and requirements. Consider potential extensions, such as integrating QR codes with other security features, to enhance document security further.
MISTAKE #5: Not Looking at System Design Comprehensively

Here’s what you can do:
Solution: Take a holistic approach to system design. This includes considering the entire lifecycle of a document, from creation to storage, retrieval, and disposal. Optimize each stage to ensure maximum document security, and plan for future updates and improvements.
In conclusion, a well-thought-out QR code strategy is essential for document security. By avoiding these common mistakes and implementing the suggested solutions, you can create a more secure and efficient document security system that meets your organization’s needs.
You may also like -
- A Definitive Guide to Using QR Codes
- Top 4 Myths about QR Codes
- Ten amazing uses of QR Codes in the industry that you may never have…
- Why does Secure QR code score over Blockchain ?