Data Privacy and Security at Qryptal: Your Trust, Our Commitment 🛡️
- Qryptal Team
- Oct 15, 2025
- 3 min read
Inside Qryptal’s approach to protecting data
In today’s digital world, data privacy and security are not optional — they are essential.
At Qryptal, we take this responsibility seriously. Whether you use our Qryptal Secure Code Service APIs or our Dash2 Web UI for generating digitally signed Secure Codes, our guiding principle remains constant.
Our infrastructure, products, and processes are built with privacy-by-design and security-by-default principles. Here’s how we ensure your trust.
🔐 1. API-Based Secure Code Generation – We Never See Your Data
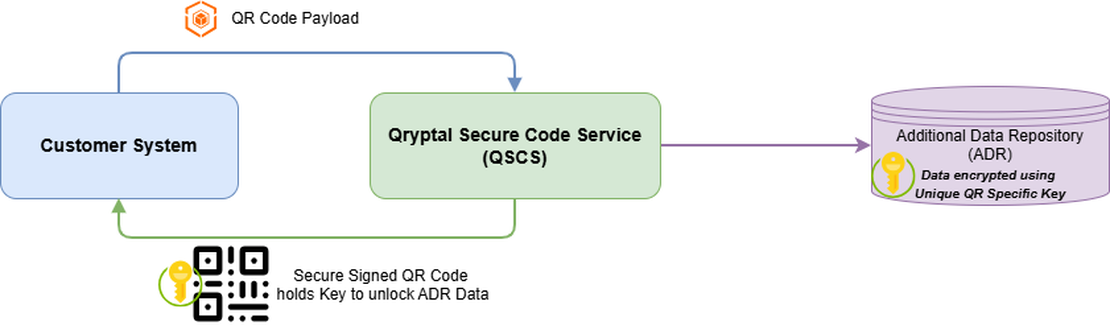
For organizations using our Qryptal Secure Code Service (QSCS) via API integration:
- Qryptal acts purely as a processing platform — not a data warehouse.
- We do not log, store or retain any end-user data in a form accessible to Qryptal.
- All data required for QR code validation is encrypted using a unique, QR-code-specific key — a key that is securely embedded within the QR code itself and not stored anywhere else.
- Even if encrypted data reside in our system, Qryptal cannot decrypt or read them — ensuring complete data confidentiality and customer sovereignty.
- We also provide an option store this encrypted data in your own cloud storage (e.g. AWS S3, Azure Blob Storage etc.).
🧩 In short: You control your data and decide who can access it.
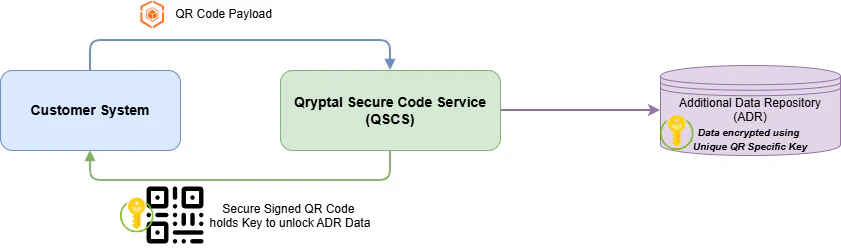
🔒 API Users – Zero Data Visibility: Only encrypted data is stored; each QR code contains a unique encryption key.
🌐 2. Web UI for Secure Code Generation – Data Handling with Full Transparency
For users who generate Secure Codes and Documents directly through our Web UI, we offer flexible and secure workflows:
- Users can generate secure codes and documents one at a time or in bulk via file upload.
- To process these requests, our system collects input data.
- We retain this information only as long as necessary to complete the operation.
- Users can define their own purging policy — as low as 1 hour — to ensure automatic deletion after processing.
- After the purge, the only data that remains is the encrypted data tied to the individual QR codes/documents held by users.
⚙️ This gives you full control:
✅ Minimal retention → ✅ Configurable purging → ✅ Encrypted persistence only
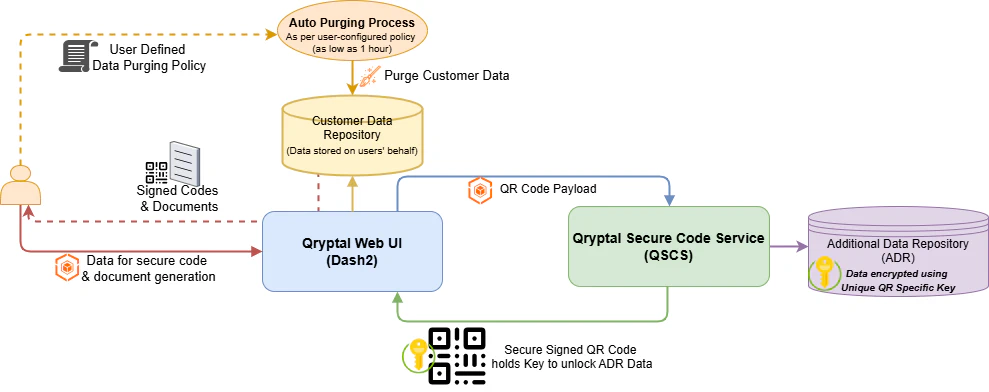
🧹 Web UI Users – User Data with configurable purge and minimal retention.
🧠 3. Built-In Privacy and Security Principles
Every part of the Qryptal platform embodies our privacy philosophy:
| Principle | How Qryptal Implements It |
|---|---|
| Data Minimization | We collect and store only what’s essential for code generation. |
| Encryption Everywhere | All sensitive data is encrypted in transit (TLS 1.3) and at rest (AES-256). |
| Access Control | Only authenticated and authorized users can access their own encrypted data. |
| Transparency & Auditability | Logs are maintained securely and periodically reviewed for compliance. |
| User Empowerment | Customers configure purging policies. |
🧭 4. Why This Matters
Organizations today face stringent compliance expectations — from ISO 27001 to SOC 2 to data protection laws like GDPR, HIPAA and PDPA.
By ensuring no unencrypted customer data is accessible to Qryptal, we make it easier for your business to stay compliant while leveraging cutting-edge Secure Code technology.
💡 5. Closing Note
At Qryptal, security is not a feature — it’s our foundation.
Every QR Code you generate through our platform is backed by layers of encryption, access control, and transparency. Whether you’re integrating via API or using our Web UI, you can rest assured your data is private, encrypted, and in your control.
Recommendation: You may like to explore more …
Evolving Needs of Document Verification in Digital Transactions
Discover the Variety of Secure QR Codes
Maximizing QR Code Security (Why your QR strategy cannot be an afterthought)
Top 4 Myths about QR Codes
Secure QR – Can AI help detect malicious QR codes?
Hybrids in QR Code – HDC