Massive Purchase Order Scam hits suppliers
- Rajesh Soundararajan
- Aug 27, 2019
- 3 min read
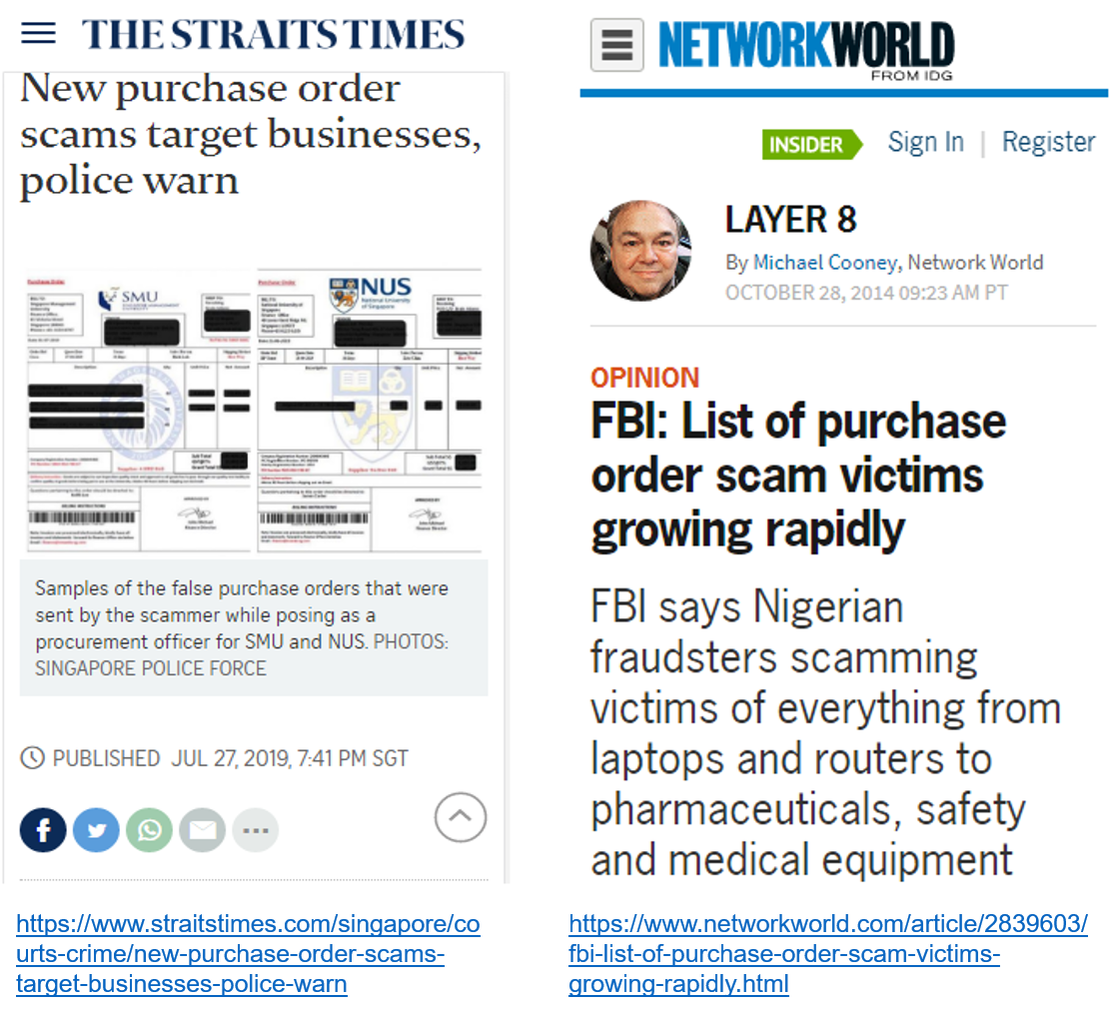
FBI and Singapore Police unearth the modus operandi
A purchase order scam of mammoth proportions and how secure QR Code can help
When the FBI launched its massive probe on purchase order scam, it was not without reason. The FBI said there were more than 85 companies and universities nationwide, in the USA, whose identities were used to perpetrate the scheme. Approximately 400 actual or attempted incidents have targeted some 250 vendors, and nearly $5 million has been lost so far.
Similar scams are being unearthed on the other side of the world, in Singapore, where companies are being advised to verify the sender’s domain name and authenticity of the request by contacting the universities via their official contact numbers, instead of trusting credentials provided in the e-mail.
For FBI or Singapore Police to call these a scam, warrants attention and is a warning for companies across the world to look at ways in which these scams of purchase orders (or similar documents) could be impacting their businesses.
The scam would look something like this -
Scammers would pose as procurement officers from local universities (as happened in Singapore) and fool unsuspecting companies/suppliers into delivering goods with promises of future payments. Companies would receive e-mails purportedly sent by a procurement officer from a local university, asking for quotations for items such as electronics. The scammers would use e-mails with the template “procurement@ edu-sg.com”. A purchase order would be sent to the company via e-mail once the agreement is made. The Purchase Order would be very similar to the original ones used by universities. Fooled into believing that a genuine Purchase Order has been issued, the supplying company would deliver the goods to the stated address. Investigations have revealed that the address indicated usually belonged to freight-forwarding companies engaged by scammers to ship the goods overseas. No payments were eventually received.
How do we stop being a party to such scams?
A simple, effective way of addressing this issue is for companies to use secure QR code in their documents, like purchase orders, as a standard practice. The critical details of the purchase order would be secured inside the QR code and can be verified instantaneously on demand. So, all vendors servicing the PO would automatically validate the PO by scanning the QR code. The QR code which is generated from the contents of the real/original purchase order and digitally signed by the private key of the issuer can be validated only by a dedicated authorised app which carries the corresponding public key and uses the PKI infrastructure for this purpose. The contents of the QR code are cryptographically secured with high levels of security and thus cannot be tampered with. This allows all the stakeholders in the chain to have trust in the documents and process the same with full confidence.
The simple system works as shown below
Such a secure QR code-based system can work both online and off-line. It would be simple to verify & make it practically impossible for fraudsters to skim and swindle from reputed companies in the manner we see in these articles. It is also easy to implement and very cost-effective. And to top it all - its a commercially tested technology. QR codes have become ubiquitous and its time to use them in the right manner with adequate security to generate trust and confidence in day to day transactions.
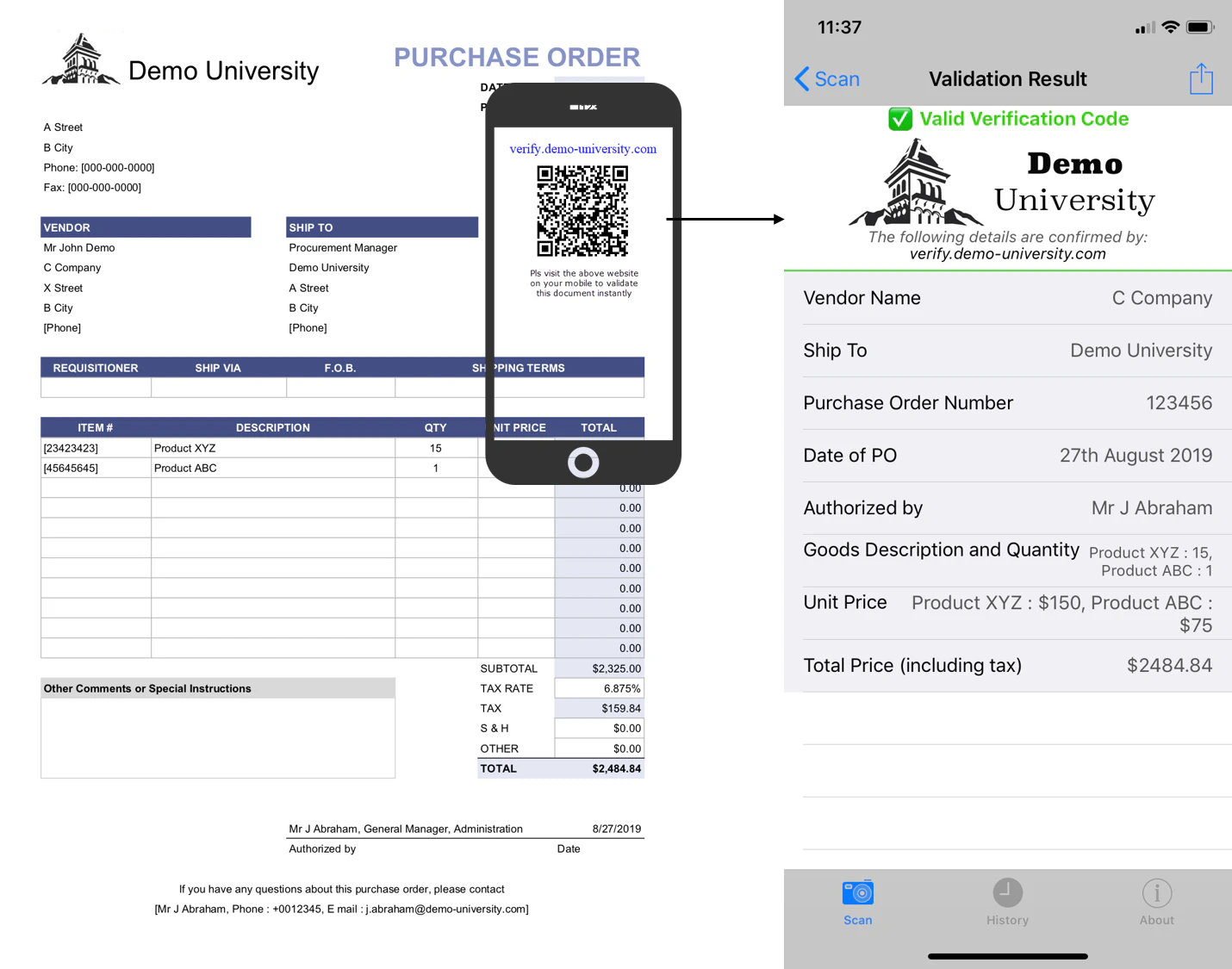
University Purchase order with Secure QR code
You may also want to read -